Table of contents
- GraphQL at scale with Azure API Management
- Landing safely with Azure Integration Services
- What’s new and upcoming in Azure Event Grid
- How can Turbo360 help me on my BizTalk to AIS journey
- Implementing Security in your AIS Solutions
- Azure Integration Services: End to end management and monitoring scenarios
- AIS common security pitfalls
After successfully concluding Day 1 & 2, we had an exciting Day 3 of INTEGRATE 2023 with some awesome sessions, powerful demos, and of course many updates from Microsoft Product Group.
#1: GraphQL at scale with Azure API Management
Toon Vanhoutte kickstarted the Day 3 of INTEGRATE 2023 about GraphQL at scale with Azure API Management.
What is GraphQL?
GraphQL is a query language invented by Facebook for APIs. It provides a runtime for fulfilling the queries with your existing data.
Here are its other exceptional features:
- There is no over fetching of data whereas in REST API, when you request something, you get the complete resource.
- Get many resources in a single request.
- A strong type system is present, and it helps to query efficiently
- A feature called mutation is available, which helps to create/update data
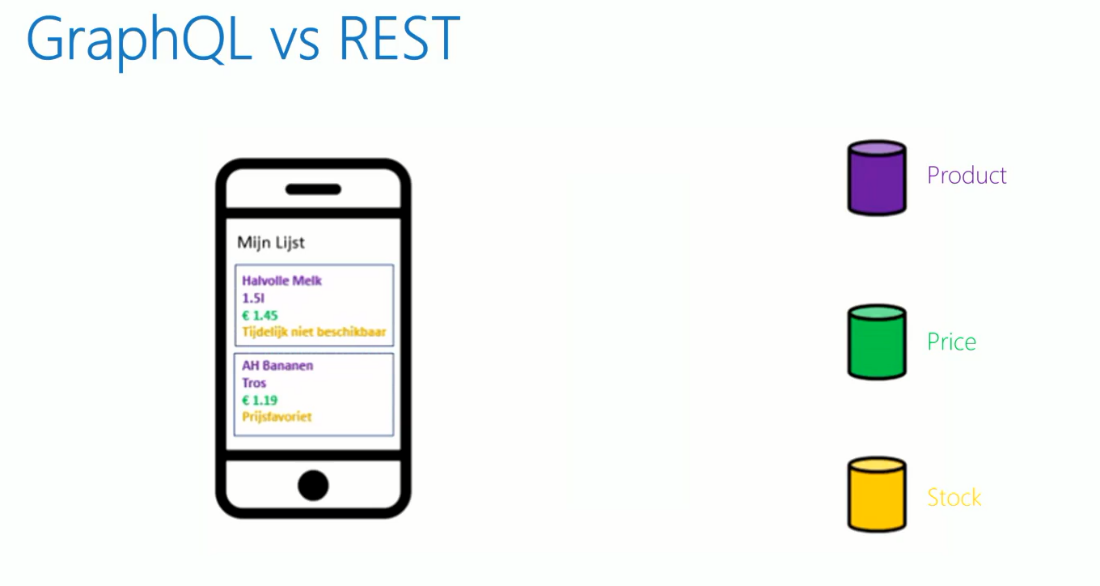
GraphQL vs REST
In REST, the client must do the orchestration by going through product API, Price API and Stock API separately to get the desired result, whereas in GraphQL, the orchestration is done by a single gateway.
One call to the gateway and it will do the orchestration and fetches only the data requested by clients. Thus, GraphQL is easier from a client perspective and more optimized.
Some of the leading organizations use GraphQL, which includes Facebook, Twitter, PayPal, LinkedIn, GitHub, Audi and Starbucks.
Challenges in GraphQL
Learning curve
Every technology will have frequent updates, and these are some of the resources to get started with GraphQL
API Design
Creating the GraphQL schema can be a cumbersome task. Luckily there is an open-source project called the GraphQL voyager which helps to visualize the schema.
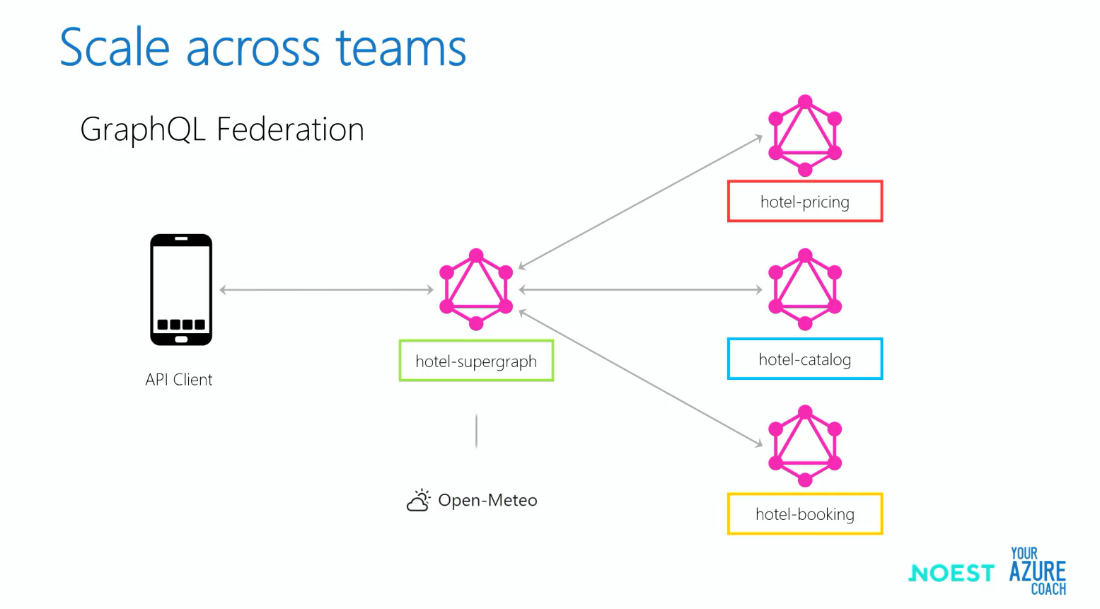
Scaling across teams
Scaling the operations among multiple teams can be quite challenging, with different teams and domains involved. This is where GraphQL Federation helps by dispatching the request to different microservices and merges all the responses and delivers it to the client.
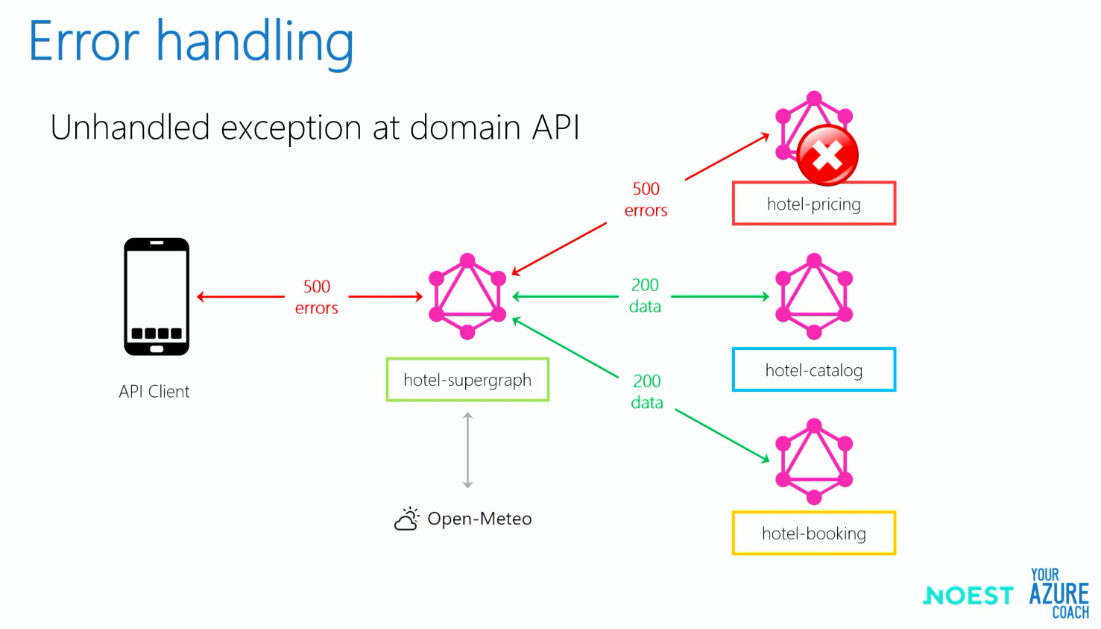
Error handling
In the example below, there was an unexpected error in the hotel pricing API request and the other two API requests were successful.
In this case, the client should be getting error message only for the pricing API. But, since even the other 2 API requests go through the same GraphQL gateway, they all will be a throwing exception. To overcome this, the speaker suggests to use custom response formatter.
Performance
There are certain performance issues one could experience when configuring multiple resolvers while using GraphQL. However, this can be mitigated using the DataLoader feature, which batches individual resolver requests into a single database query and sends it to the backend.
Security
Both Azure API Management and Azure Active Directory can be used to improve security when it comes to using GraphQL.
These above are some of the challenges in GraphQL and last but not least, Toon concluded by saying that “the world is organized around REST, but GraphQL is coming”.
#2: Landing safely with Azure Integration Services
Dan Toomey provided a continuation from day 2’s discussion on “why is integration so hard? “’
He highlighted various design areas and shared better ways to utilize them within the cloud architecture framework.
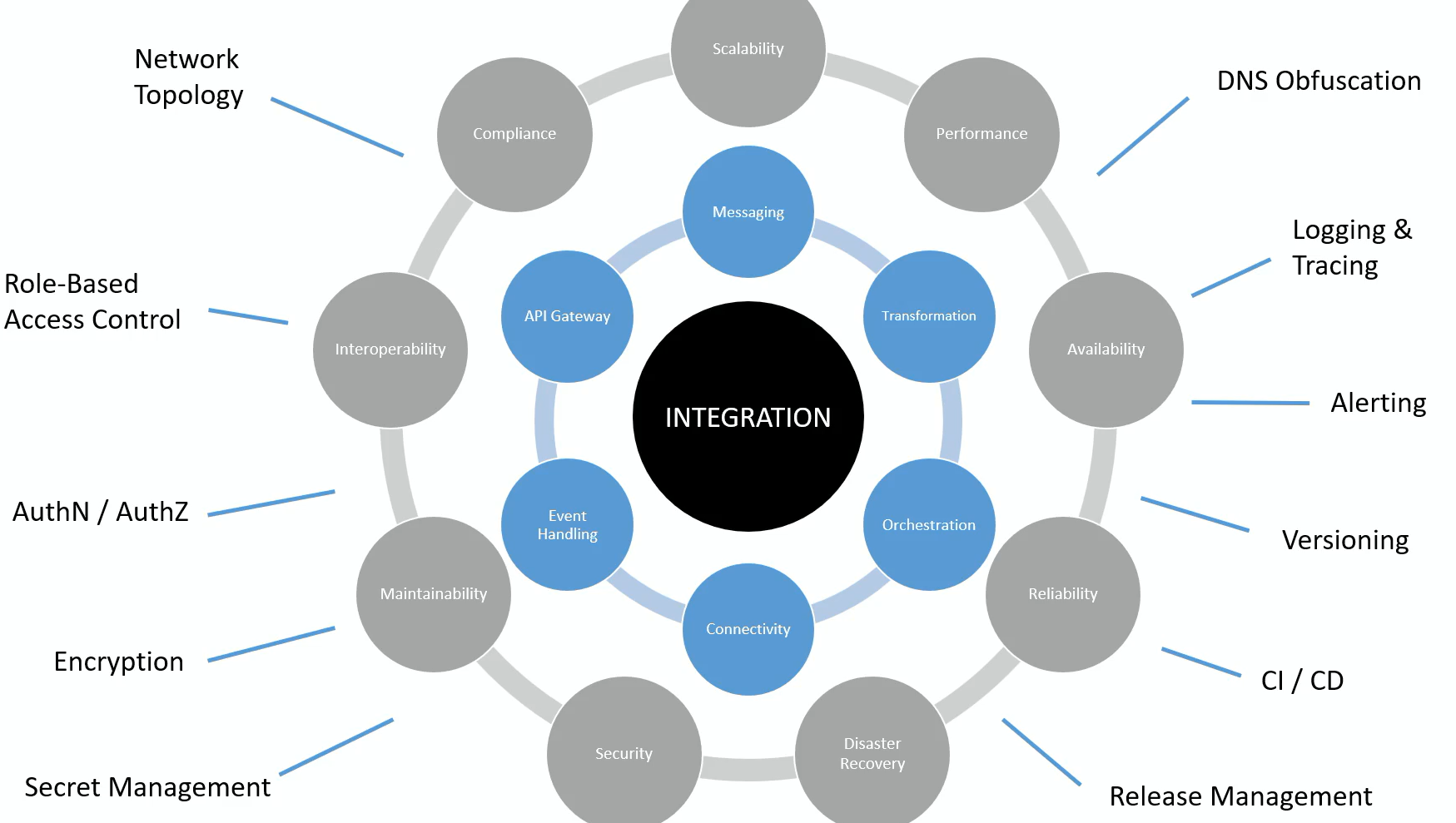
Azure landing zone:
The landing zones are a pivotal component of the Cloud Architecture Framework, as it is scalable and modular to meet the deployment needs. It includes two types: Platform landing zones and Application landing zones.
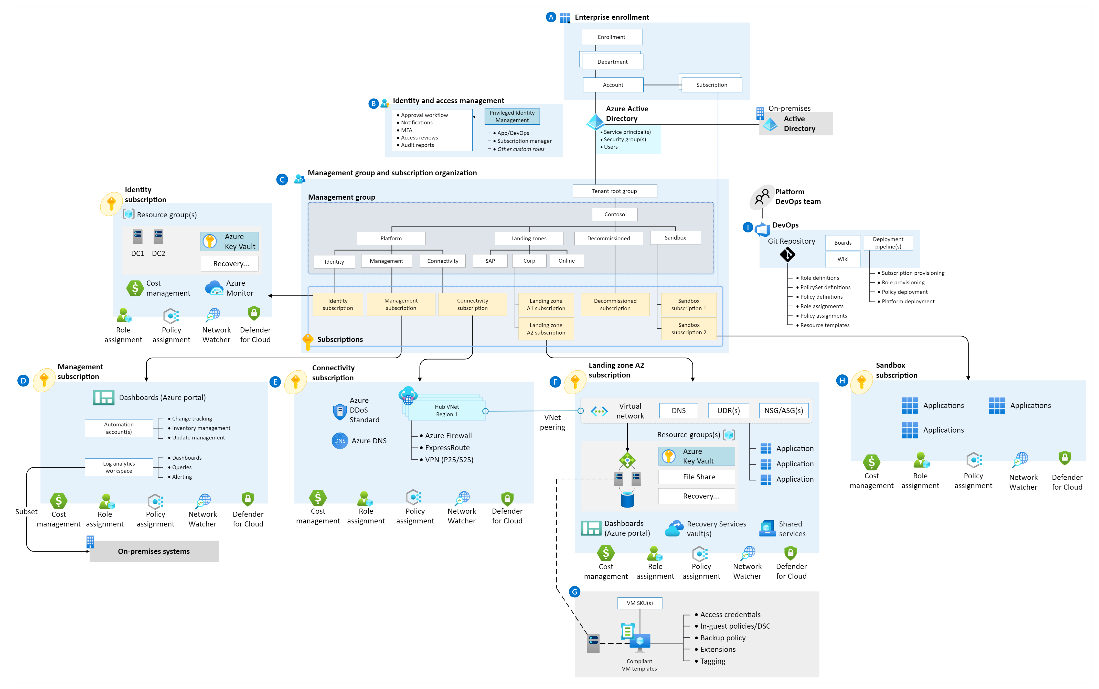
Azure Integration services landing zone:
The Azure Integration Services landing zone was established a few months ago, and it offers a streamlined approach to automate the implementation of an enterprise integration platform. He thoroughly explored six design areas and shared best practices for design considerations and recommendations.
Key highlights:
Identity and access management:
Design considerations: Determine resource administration boundaries, review activities and distribute responsibilities effectively.
Design recommendations: Identify roles needed for AIS applications, consider log file and data access, define access privileges, utilize custom roles, and enforce compliance using Azure Policy.
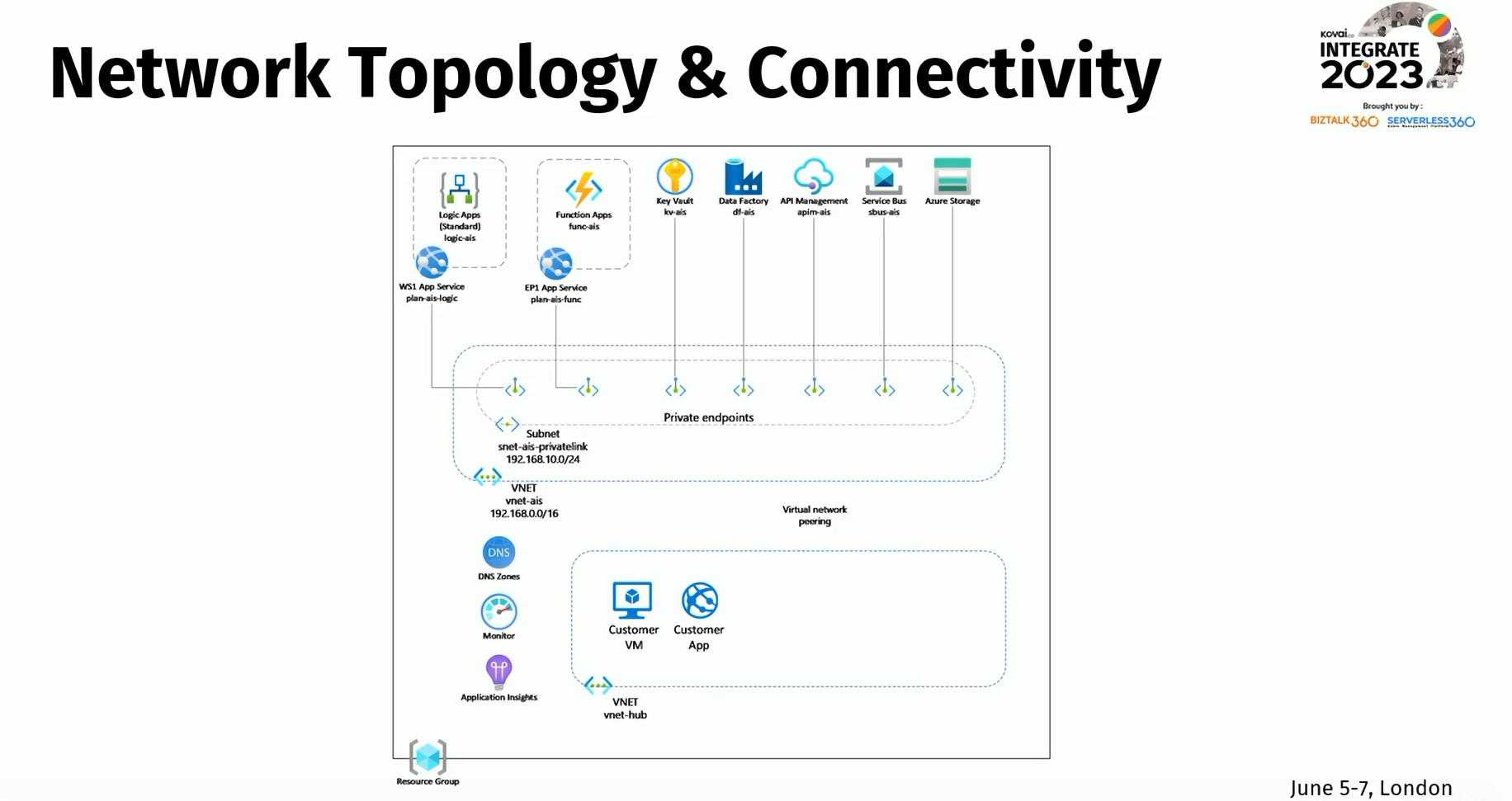
Network topology and connectivity:
Design considerations: Choose between traditional hub or spoke architecture or a virtual WAN for your network design.
Design recommendations: Carefully plan for IP addressing, implement custom or private DNS, ensure encryption, and certificate authentication, and establish connectivity to on-premises systems.
Security:
Design considerations: Choose between private, public, or hybrid cloud deployment based on resource visibility and accessibility. Consider DNS obfuscation for public resources to enhance security.
Design recommendations:
- Utilize managed identities for resource access.
- Enable encryption at rest and in transit for data storage
- Leverage Application Gateway or Web Application Firewall for endpoint protection
- Use Azure Policy for security checks. Utilize Azure Key Vault for secrets.
- Implement OAuth 2.0 for authentication
Management:
Design Considerations: Determine monitoring needs, resource tracking, alerts, and dashboards. Identify management tasks and message tracking requirements.
Design Recommendations: Use Azure Monitor or tools like Turbo360 (An advanced Cloud Management platform for Microsoft Azure) or you can set up Application Insights with Log Analytics for centralized storage.
Governance
Design Considerations: Ensure compliance with legal, financial, and regulatory requirements. Define roles and responsibilities. Establish a disaster recovery plan or implement alert/escalation processes.
Design Recommendations: Use Azure Policy to enforce standards and assess compliance. Implement RBAC for access control. Use Monitoring Tools like Turbo360 and Microsoft Defender for Cloud to identify policy breaches and security issues.
Platform automation and DevOps:
Design Considerations: Plan for DevOps and automation using Infrastructure-as-Code. Address the limitations in CI/CD environments and then implement CI/CD with automated testing and deployments.
Design Recommendations: Adopt early deployment. Use trigger-based and scheduled pipelines. Separate infrastructure and application deployment. Test business logic and perform load tests. Implement peer review and the 4-eyes principle. Establish processes for quick fixes. Explore landing zone accelerator recommendations.
He highlighted the process of deploying the resources needed for Enterprise-ready AIS installation through a series of deployment templates that are readily available in the GitHub public repository. Additionally, he discussed how to utilize GitHub’s project board.
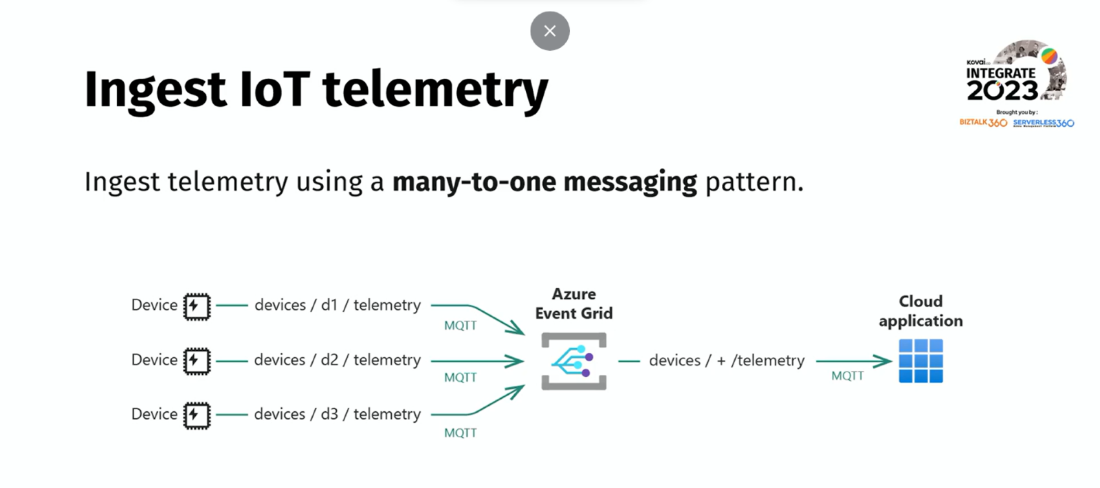
#3: What’s new and upcoming in Azure Event Grid
George Guirguis, Product Manager from Microsoft, began the session by providing an overview of Azure Event Grid.
He then proceeded to share updates on the newly released features for Azure Event Grid that are currently available for public preview. Here are following features have been mentioned:
- HTTP event push delivery
- HTTP events pull delivery
- MQTT support
HTTP event push delivery:
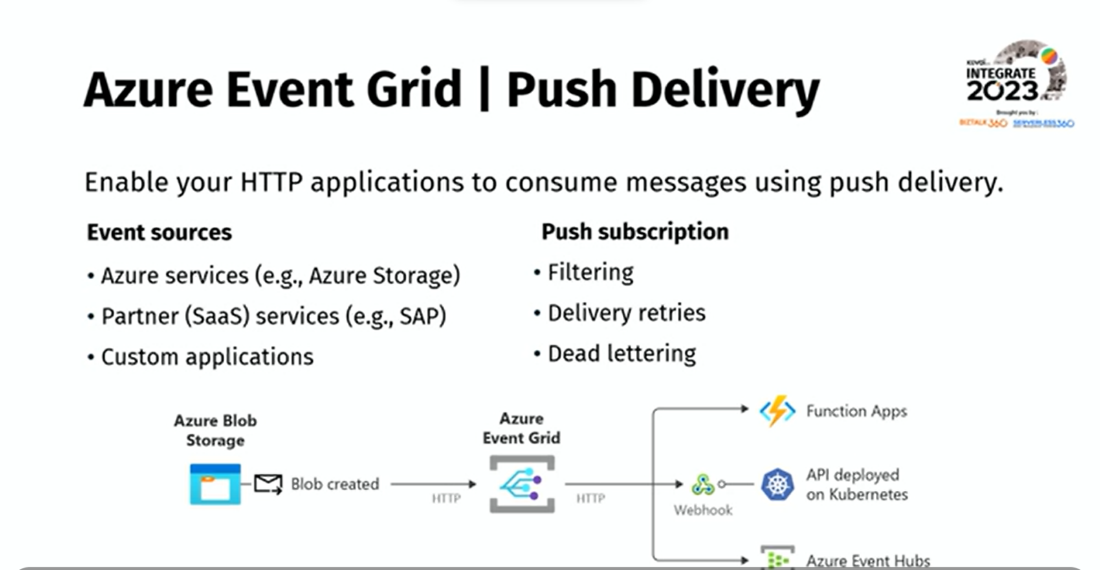
Push delivery in Azure Event Grid allows one to specify a destination for events in an event subscription, such as a webhook or an Azure service. It is supported across custom topics, system topics, domain topics, and partner topics.
HTTP events pull delivery:
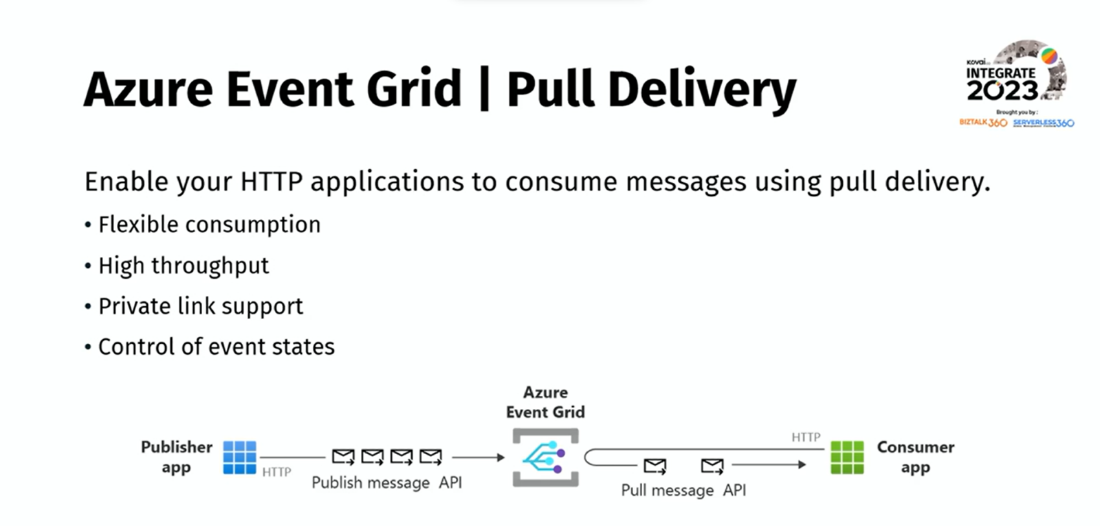
In push delivery, Event Grid actively pushes events to subscribers’ endpoints through HTTP POST requests. This approach is suitable for real-time event processing and enables subscribers to actively retrieve events from a source or service. Furthermore, it allows subscribers to periodically request events from the event source or service using a pull model.
He emphasized the introduction of a new Event Grid resource known as the “Event Grid namespace”, which serves as a container specifically designed for hosting pull delivery functionalities and MQTT messaging. Continuing that, he gave a demo on the pull delivery feature using the Event Grid Namespace.
MQTT support:
Message Queuing Telemetry Transport (MQTT) protocol is a pub/sub messaging transport protocol for constrained environments (IoT scenarios). It has become the go-to communication standard for IoT scenarios due to its efficiency, scalability, and reliability.
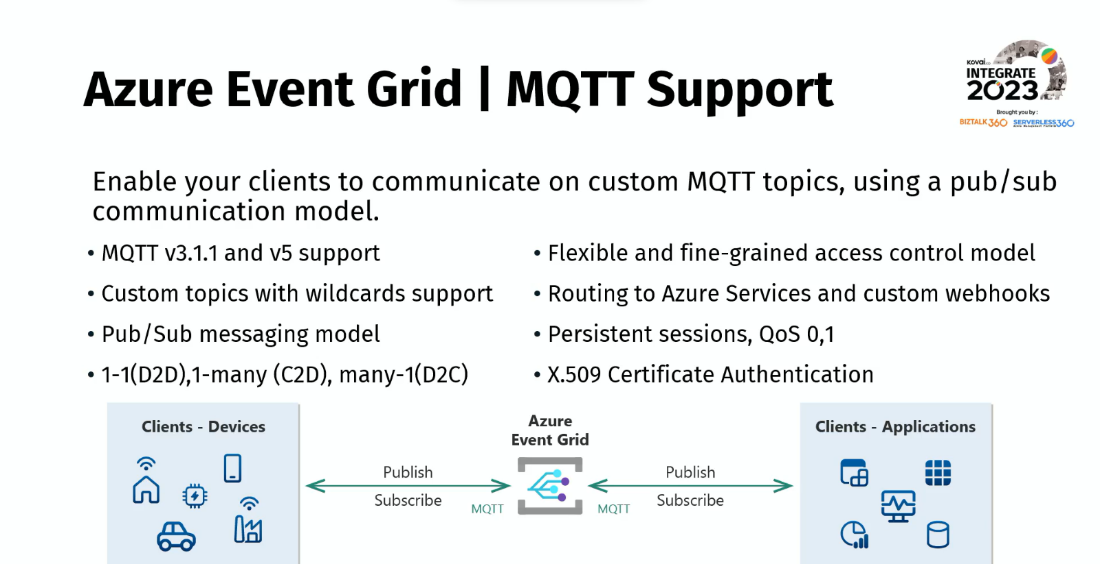
He mentioned that Azure Event Grid now has full MQTT functionality, enabling clients to communicate on custom MQTT topics, and it is currently under public preview.
Custom topics:
In Azure Event Grid, custom topics allow the creation of event sources and publish events to those topics. Custom topics provide flexibility in defining and publishing events for specified scenarios.

Routing:
The routing configuration in Azure Event Grid enables sending all messages from clients to an Event Grid custom topic. Then, event subscriptions can be configured to route the messages from the custom topic to the supported event handlers.
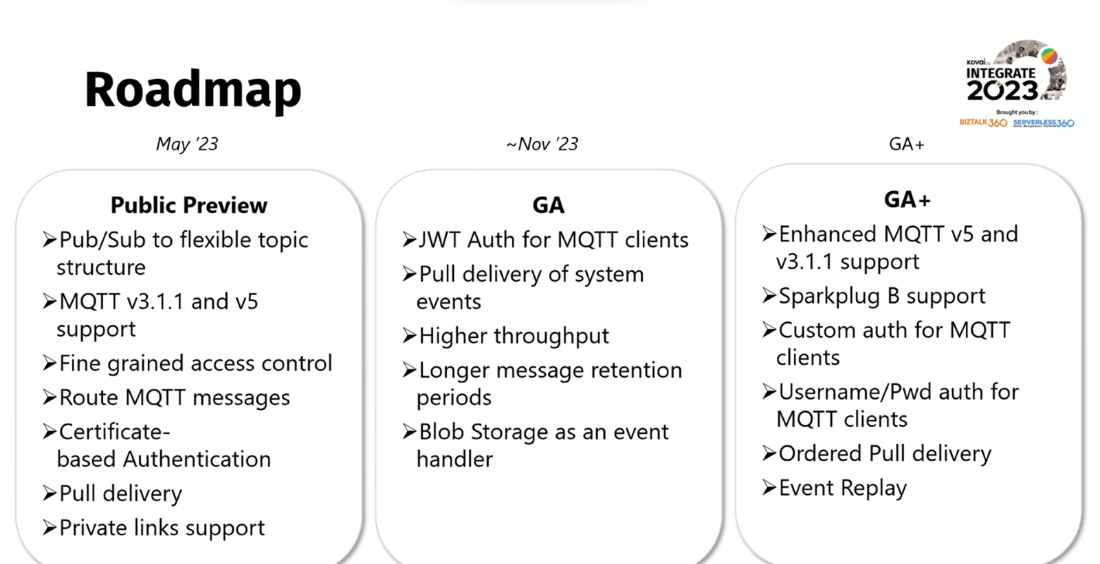
As the session came to an end, he walked through the roadmap for future updates. Furthermore, he shared Event Grid update resource articles for the new features he mentioned previously.
#4: How can Turbo360 help me on my BizTalk to AIS journey
Michael Stephenson, Integration Consultant, commenced the session by shedding light on how migration from BizTalk to Azure can be made seamless with Turbo360.
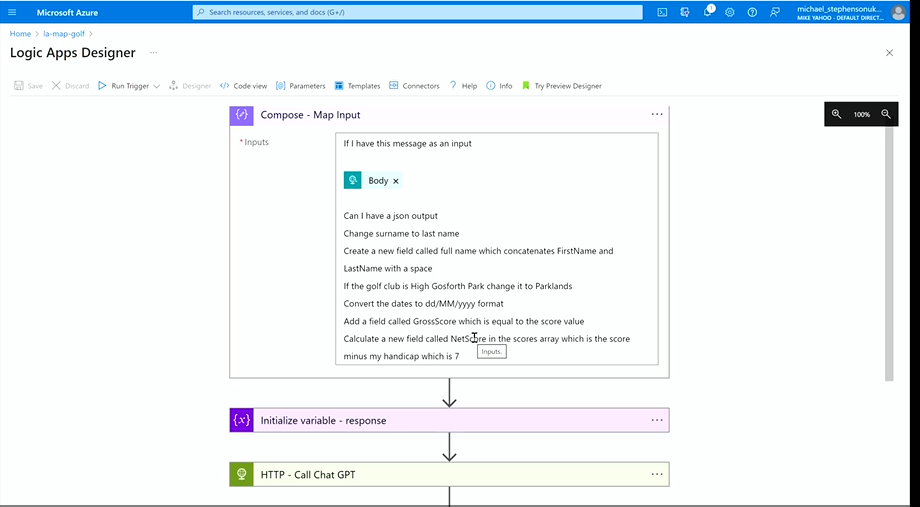
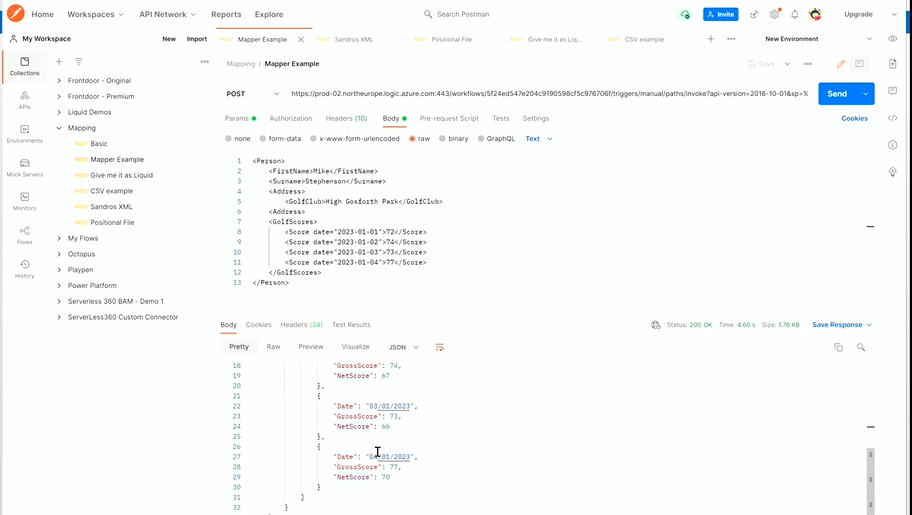
Before getting to the main session, Mike gave a sneak peek into an update on how natural language can be given as a map input to automatically generate JSON code with the help of ChatGPT. He showcased the same in the Logic Apps and Postman integration, demonstrating its capabilities and benefits.
Position of BizTalk360 in Integration Platform
Using BizTalk Server in real-time businesses posed a lot of challenges in monitoring and managing. That’s where BizTalk360 rightly helped.
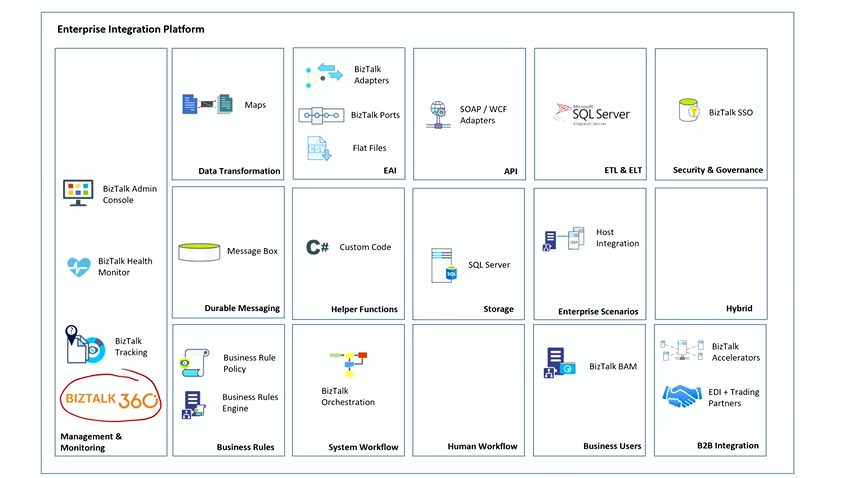
Position of Turbo360 in Integration Platform
However, he mentioned a lot of users are already in transition phase moving slowly from BizTalk Server to AIS. So, Turbo360 plays a crucial role in monitoring and managing solutions built using Azure.
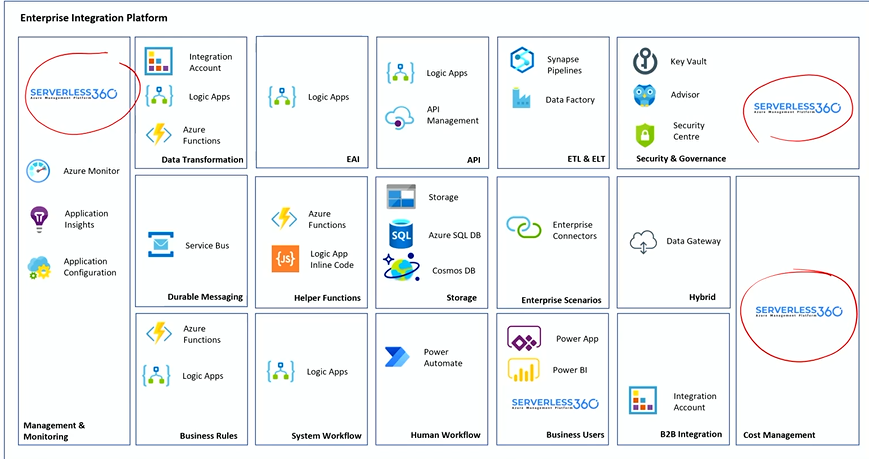
Guidance
Mike highlighted that there is no proper migration guidance for BizTalk to Azure and then discussed how Kovai.co offers an ample number of resources to make the BizTalk to Azure migration less challenging.
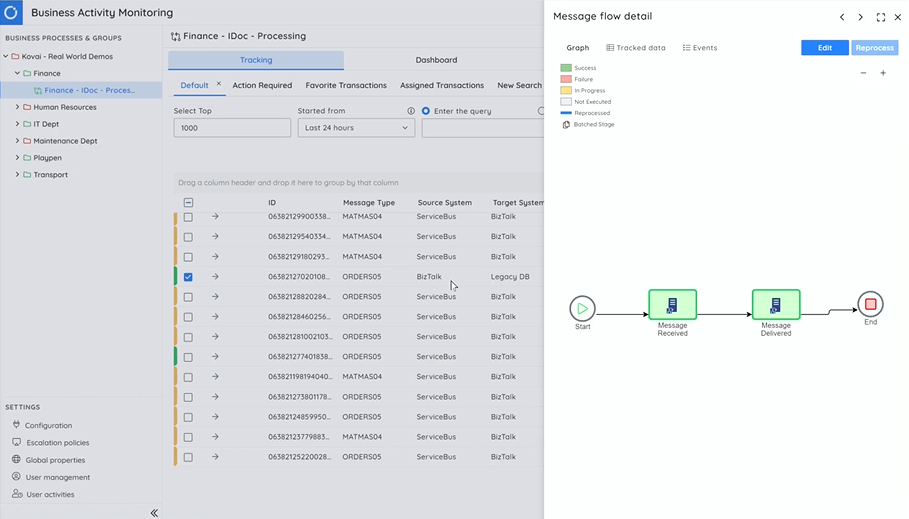
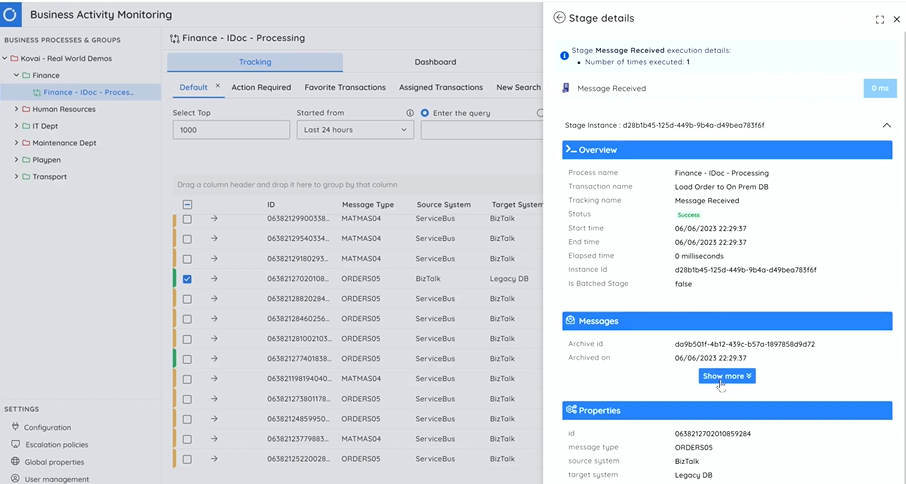
BAM for BizTalk with Turbo360 BAM
As users follow a phased migration from BizTalk to Azure, Mike demonstrated how Turbo360 BAM can be used to manage your BizTalk architecture. In the scenario, he showcased the method to pull the data from BizTalk server and publish the idocs in the Azure Integration Platform. The data from BizTalk can be integrated and monitored on a daily basis.
Business Applications (Shift-left Azure support)
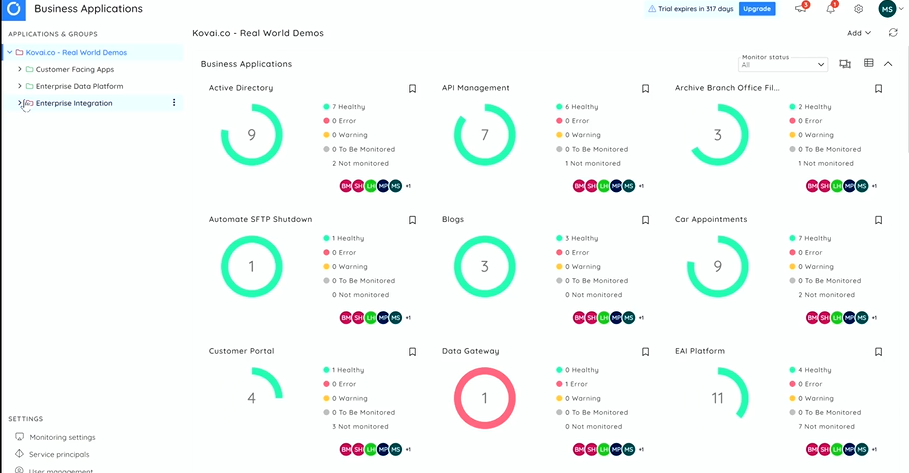
Following BAM, he showcased a demonstration of Turbo360 Business Application. He dived deep into working and the various features in Business Application. It not only supports Integration Platform but also other Data Platform and Customer Support Apps.
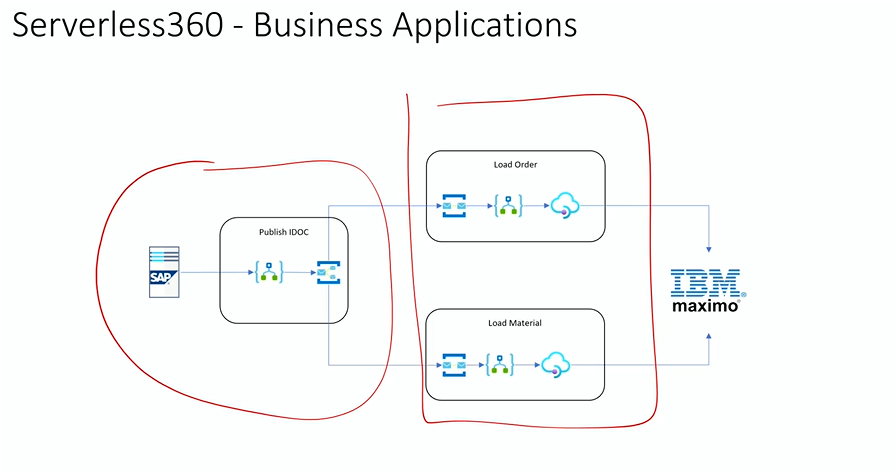
He pointed out some of the important features of the BA
- Service Map: Visualize the Azure resource with health status
- Automated Tasks: The scenario focused on the Logic Apps, and with automated tasks, you can resubmit failed Logic App runs.
- Monitoring: Monitor your resources with multiple metrics with a single alert.
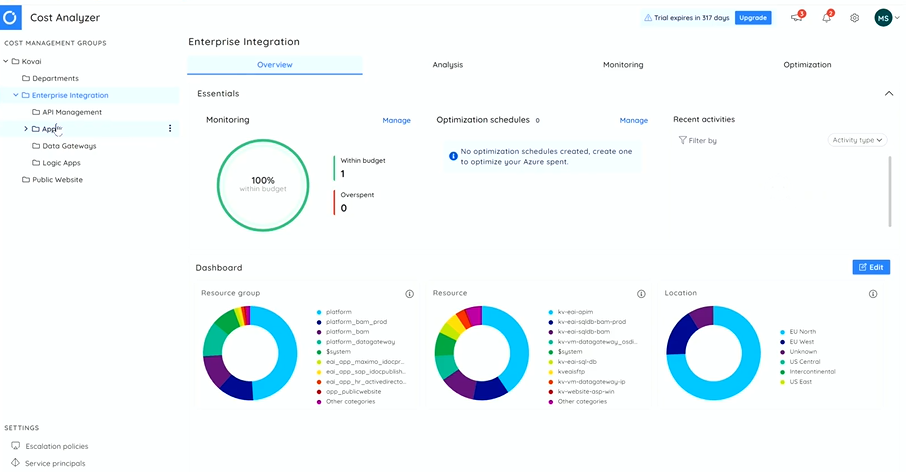
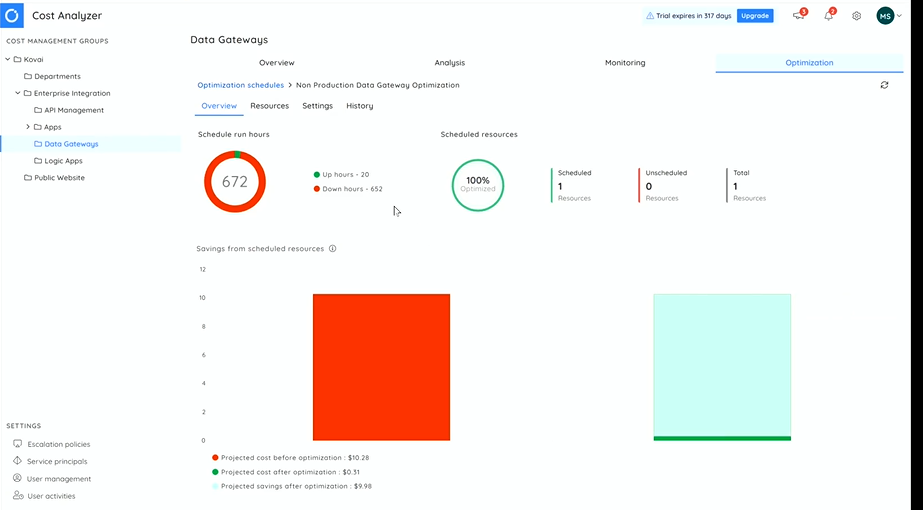
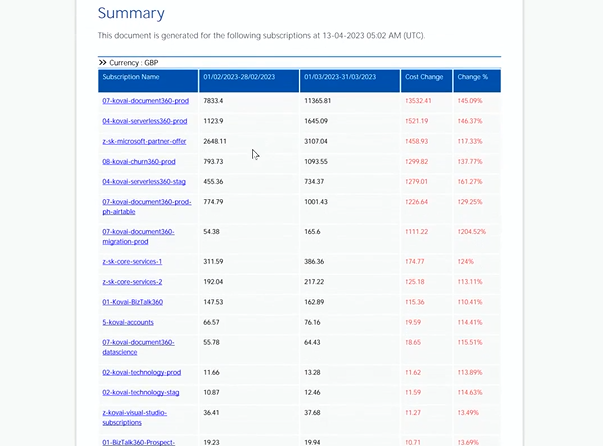
Develop a cost-focused culture with Cost Analyzer (Left shift support to FinOps)
Then, he moved on to the next module of Turbo360 which can assist Azure users to track and monitor their resources costs. The key features include Monitoring, Analyzing and Optimizing the resources across subscriptions.
Also, it enables the pause and resumes of Azure resources during non-peak hours which will eliminate the cost wastage.
Azure Documenter (Shift Left support to Decision Makers)
Mike talked about how manually documenting your entire Azure subscriptions can be quite tiresome work. Turbo360’s Azure Documenter solves that problem by automatically documenting the Azure subscriptions and keeping them up to date.
At the end, he summarized by highlighting the key features and the use cases of Turbo360 and Turbo360 addresses the gap in Azure as well as BizTalk Migration.
#5: Implementing Security in your AIS Solutions
Security is a paramount concern for businesses in today’s digital landscape. Alessandro Moura, Integration Platform Lead at Fisher & Paykel Appliances, delivered an insightful session on implementing security in AIS (Application Integration Solutions). With a wealth of knowledge and experience, he guided the audience through various security options and best practices to protect APIs, Azure resources, and network infrastructure.

Kicking off the session, he shared his journey from New Zealand to London, expressing his excitement to be part of the event. He then delved into the session agenda, emphasizing the importance of security in modern business operations.


One of the key topics discussed was protecting APIs. he highlighted the need for the right level of visibility for APIs and demonstrated how OAuth and Azure AD can be utilized to safeguard them. He stressed the significance of applying fine-grained access controls to ensure that only authorized users have access to specific APIs. The audience was excited as he provided insights into the Front Door feature, which acts as a gateway to protect and control incoming traffic.

he further explained a sample architecture, highlighting the flow of information between Azure resources and the need to protect APIs at the forefront. He showcased how businesses can ensure the right level of visibility for APIs and demonstrated the segregation of API access based on user roles. This granular access control provides enhanced security for both internal and external users.
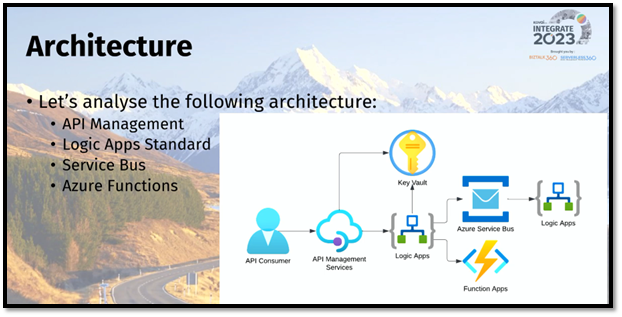
Moving on, he explored the crucial aspect of protecting Azure resources. He emphasized the usage of managed identities, specifically in Logic Apps and Service Bus scenarios. By leveraging managed identities, developers can ensure secure access to Azure resources without the need for explicit credentials. The session provided valuable insights into potential security risks such as DDoS attacks, SQL injection, cross-site scripting, and more, emphasizing the importance of implementing robust security measures.


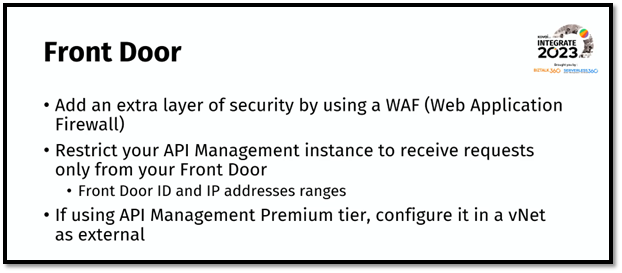
Throughout the session, he engaged the audience with interactive elements, such as showcasing an intriguing picture that related to the topic at hand. He emphasized the significance of out-of-the-box security measures provided by Azure services, such as API keys for API management, SAS keys for Logic Apps workflows, and identities for Key Vault. However, he emphasized that relying solely on these measures might not be enough, and additional security.
The session concluded with he reiterating the importance of security as an everyday practice and encouraged the audience to consider the available security options to safeguard their business operations. Attendees left the session equipped with practical insights on implementing security in their AIS solutions, ready to enhance their security posture and protect their valuable assets.
#6: Azure Integration Services: End to end management and monitoring scenarios
Wagner Silveria, Senior Program Manager at Microsoft, and Slava Koltovich, Principal Group Product Manager at Microsoft, presented the session about Azure Integration Services: End-to-end management and monitoring scenarios on day 3 of INTEGRATE 2023. In this session, they shared the latest improvements and roadmap to unlock management and monitoring of end-to-end integration applications across Azure Integration Services.
Agenda
- Introduction to unified experience concepts
- Creating apps and monitoring
- Creating Business Process Tracking
Note: The release is a work in progress and not available to the public preview, and it is only available for the Microsoft Integration groups.
They planned to have two real-time demonstrations to explain the application monitoring and business tracking process in the release pipeline.
Wagner started the session by presenting the demo, which pictured the integration Solution of Customer Service for Power Outages.
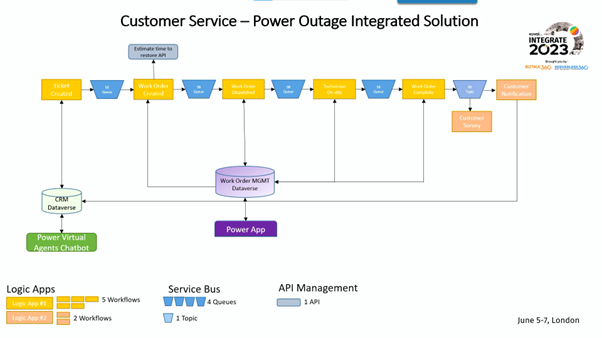
This demo covered the concept of a unified experience, where they created a new integration space, defined an integration application, and set alerts and monitoring dashboards. By the demo’s end, feedback was collected to enhance it before public use.
Then, Wagner presented a demonstration on Business Process Tracking for the same scenario.
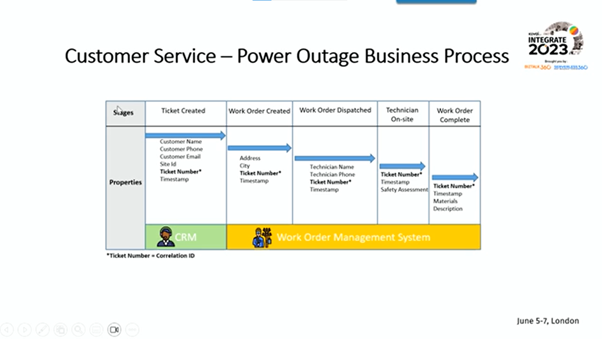
This demo showcased the creation of business process tracking, the creation of a business tracking profile, and how the transactions are reviewed. Like the previous demo, feedback was collected to enhance the release.
Finally, they showed how the tracking and monitoring would reflect in proving details in the chatbot response.
As they plan to have a private preview for the features, they concluded the session with a registration poll to understand the interest in a private preview version among the audience.
#7: AIS common security pitfalls
Mattias Logdberg, Solutions Architect at DevUP Solutions AB presented the session on AIS (Azure Integration Services) common security pitfalls on Day 3 of Integrate 2023. He began the session with the different security approaches every professional can handle in their day-to-day activities. He threw light on data breach costs with accurate reports.
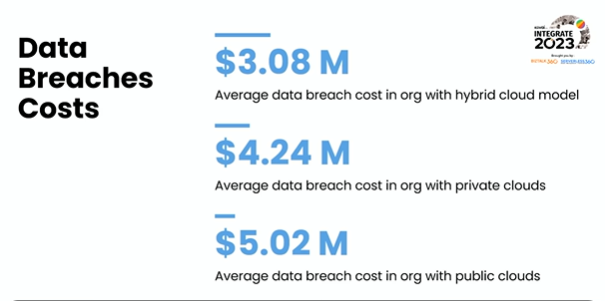
Cloud misconfiguration risk
Mattias highlighted that in a recent survey indicated that more than 90% of security professionals are concerned that human error could result in the accidental exposure of their cloud data. He emphasized a couple of human errors happened which can truly ruin the business process.
10,000,000 files leaked Hospitality Cloud Platform Data Breach caused by misconfigured S3 bucket.
Sample scenario using Storage Account
One of the most interesting and widely used by enterprises is Storage Account, hence Mattias showcased security aspects of this feature.
The first thing users need to investigate is Security in the Azure portal.
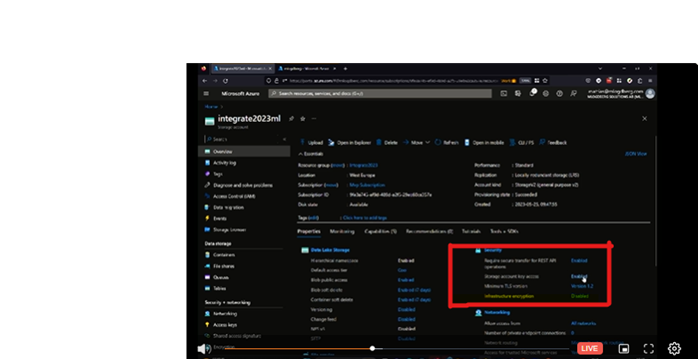
Blobs are storage containers and containers are useful for storing files. Users need to be very precise about the level of access that their team members can access. Mattias highlighted the types of public access levels to the audiences using which users can highly secure their containers. Mattias provided a simple tip for the crowd by navigating as follows:
<Container>→ Configuration→ Allow Blob public access→Disabled.
This simple switch can prevent lots of damage which made audiences awestruck for a moment.
Networking and API (Application Programming Interface) security risks
Mattias took a deep dive into networking, subnets, firewall and security risk exposure to API. He highlighted a demo of the Uber breach which was quite interesting. Using role-based access in Azure, he emphasized the importance of security with the demo. This session was more of a live demo which made audiences much more excited and resulted in exciting questions and answers.
That’s the wrap for Day 3 of INTEGRATE 2023!







